Lidl Monsieur Cuisine Smart (MCS)
Technical info
Processor: Mediatek MT8167
Security chip: Maxim Integrated DS28C36
OS: Android
OS Version: 8.1.0
Linux kernel version: 4.4.95
It’s essentially an Android tablet connected to a motor (for mixing and blending) and a heating element via serial communication.
Factory Mode
From the MCS start page, open the menu with the top-right hamburger icon:

Open “Settings”:
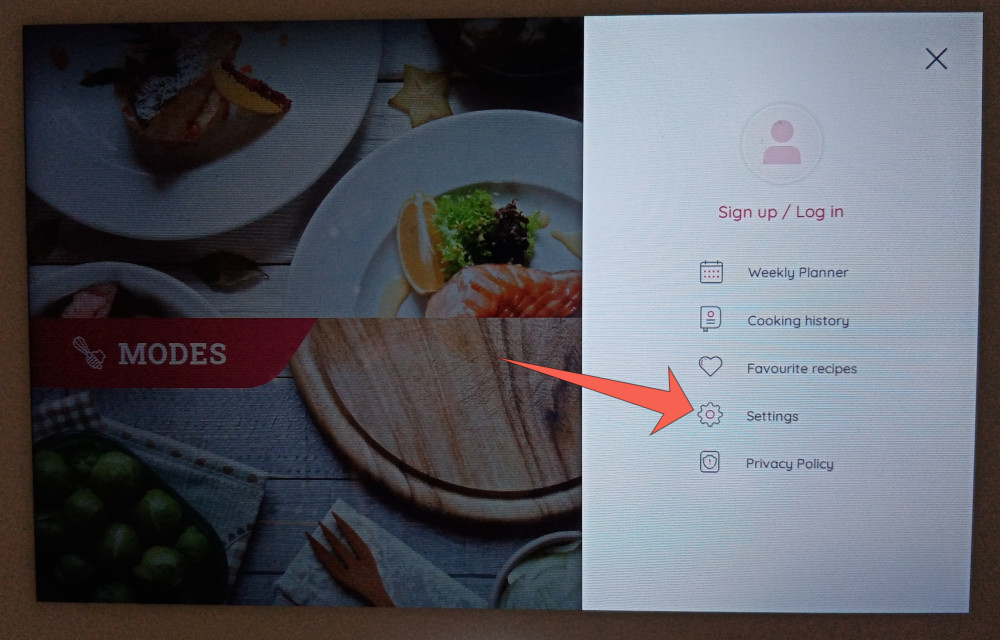
Open “About”:
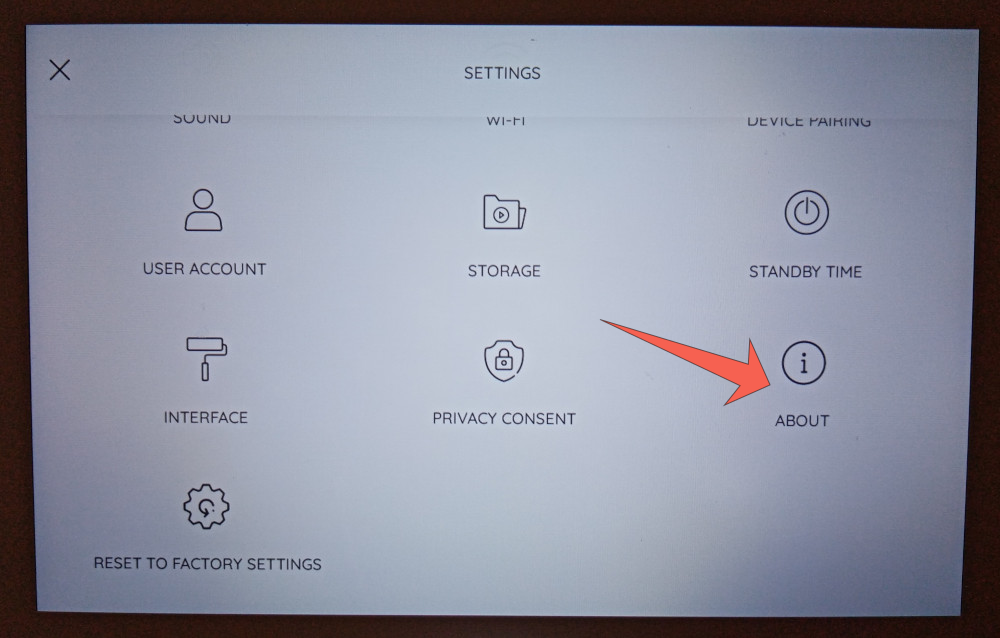
Click on “About this device”:
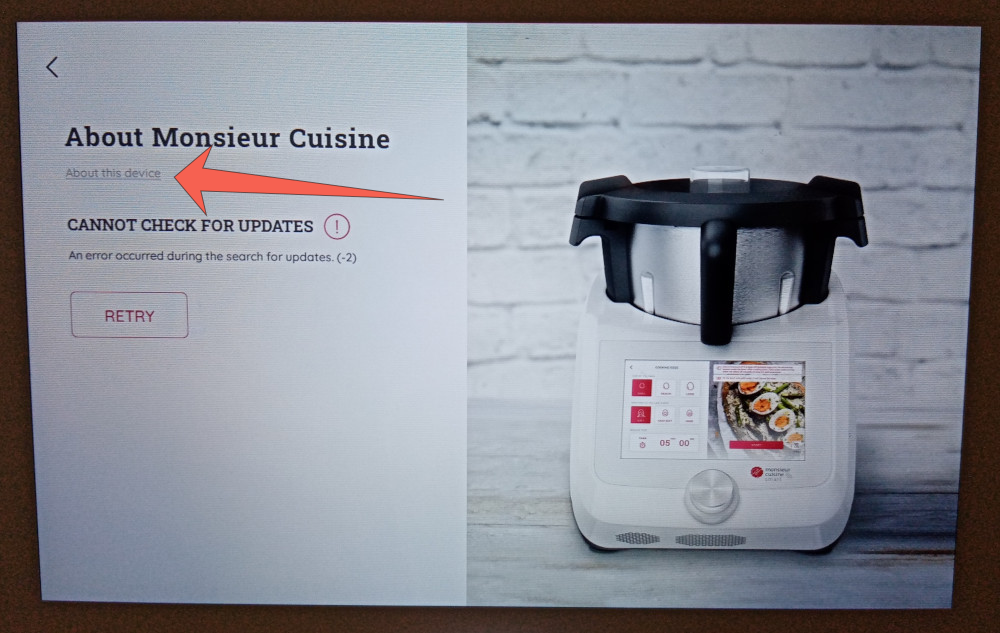
The following popup should appear, take note of the last 4 characters of the serial number (1K2W in this example), then click “Done” to return to the previous screen:
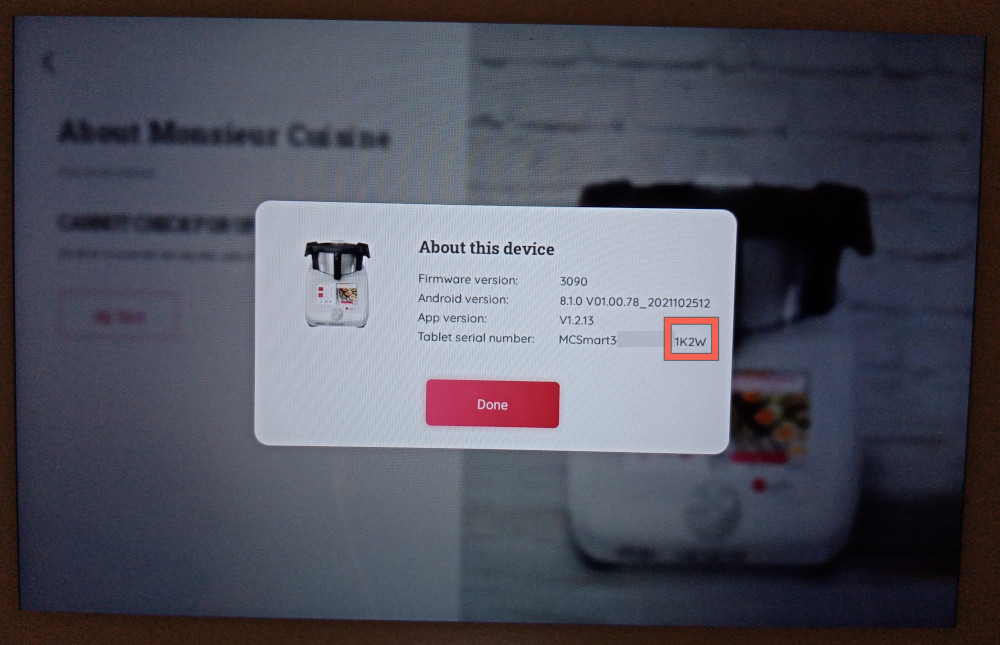
Click on the “About Monsieur Cuisine” title for about 2 seconds:
A password will be requested, the password is the last 4 characters of the serial number, followed by _Mc30 (1K2W_Mc30 in this example). Once unlocked, factory mode will be accessible without a password for the following 15 days.
From factory mode you can test the touchscreen, LCD, backlight, speaker, Wi-Fi, encryption chip, button and LED Light functionality, then access “Further test” which is more MCS specific, where you will find:
- Scale calibration (using 1kg and 3kg weights)
- Endurance test
- Wi-Fi test
- Scale test
- Device activation (you won’t be able to do much here: the device should already be activated)
- Security chip test
From the “Further test” screen you can access Android settings by clicking on the version number in the bottom right corner for about 2 seconds, from which you can enable developer mode…
USB Port
Underneath the device, and a small plastic “maintenance” cover, protected with a single torx screw, you will find two USB ports:
- Power PCB USB: Avoid using this port as it could fry your device
- Android USB

After connecting a computer via the appropriate cable to the “Android USB” port, upon turning on the MCS, an “MT65xx Preloader” should pop-up on the computer for about 2 seconds. Using tools (such as SP Flash Tool) it’s possible to upload / download data from the MCS.
Security chip
The device contains a Maxim Integrated DS28C36 security chip, accessible via I²C and used in this particular context to sign and / or encrypt certain API requests. It appears that device enrolment / activation is only possible via a dedicated Wi-Fi network at the factory, this process involves generating a key pair for the device and sending the public key to the server, along with the device’s serial number.
It’s actually suprisingly well protected and thought through, although if you are able to run your own code on the device, you can also access the security chip and the device keys.
Protected API endpoints:
api/v2/users/loginapi/v2/bookmarks/api/v2/bookmarks/syncapi/v2/bookmarks/details/page/{page}/size/{size}iot/v2/confirmedCommandapi/v2/devices/nameapi/v2/devices/resetiot/v2/confirmDevicePairingiot/v2/pairDeviceiot/v1/sendCommandapi/v2/devices/statusapi/v2/apps/users/loginapi/v1/authkey/addapi/v1/authkey/response-keyapi/v1/authkey/signature-keyapi/v1/authkey/reset-response-keyapi/v1/authkey/verify-hub-keytms/v2/cooking-historyapi/v2/userschange-passwordapi/v2/users/loginapi/v2/userslogoutapi/v2/tokens/refreshapi/v2/usersreset-passwordapi/v2/users/social/loginapi/v2/apps/{packageName}/version/signature/{signature}api/v2/users